ICCK Transactions on Cybersecurity | Volume 1, Issue 1: 17-34, 2025 | DOI: 10.62762/TC.2025.281528
Abstract
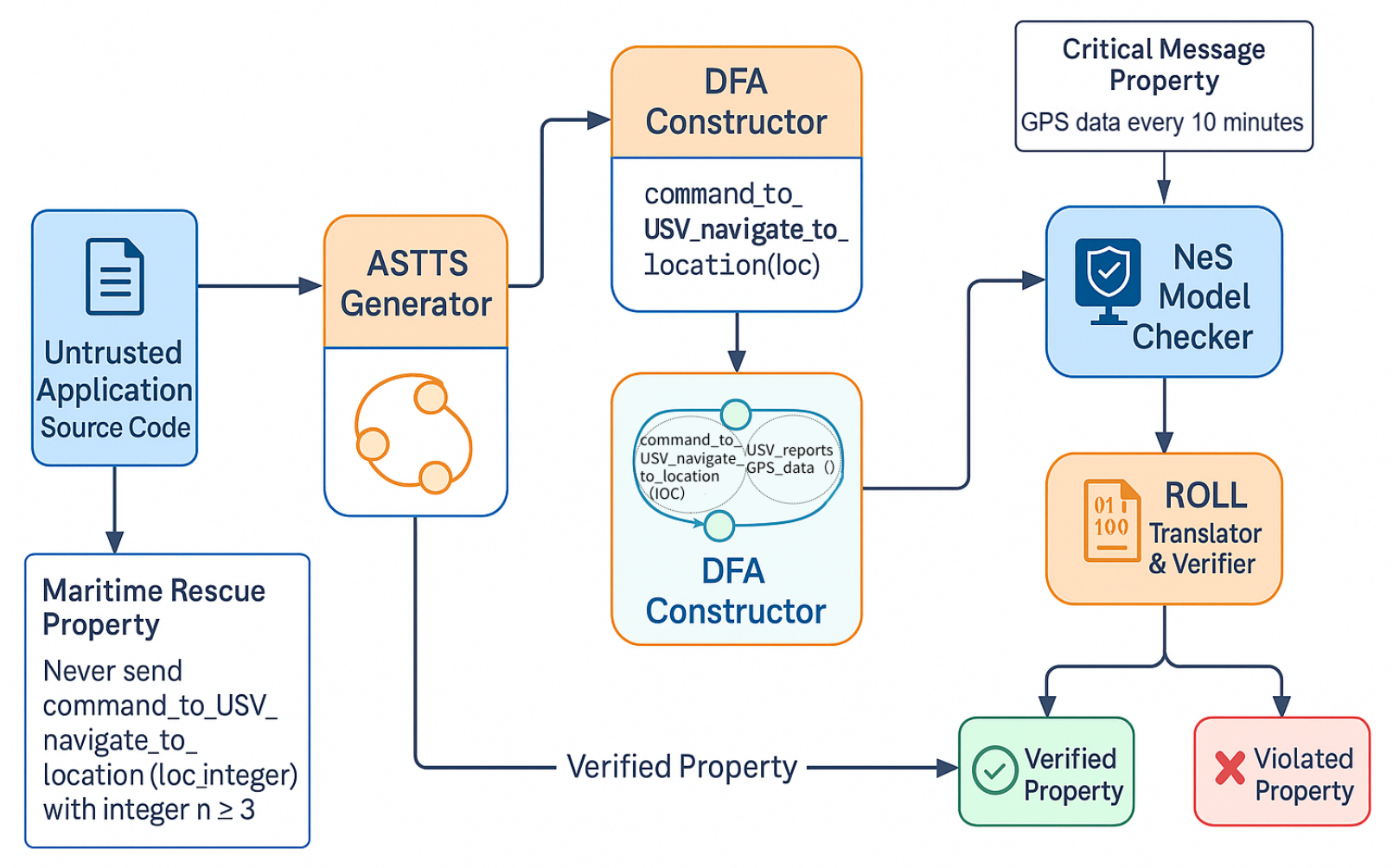
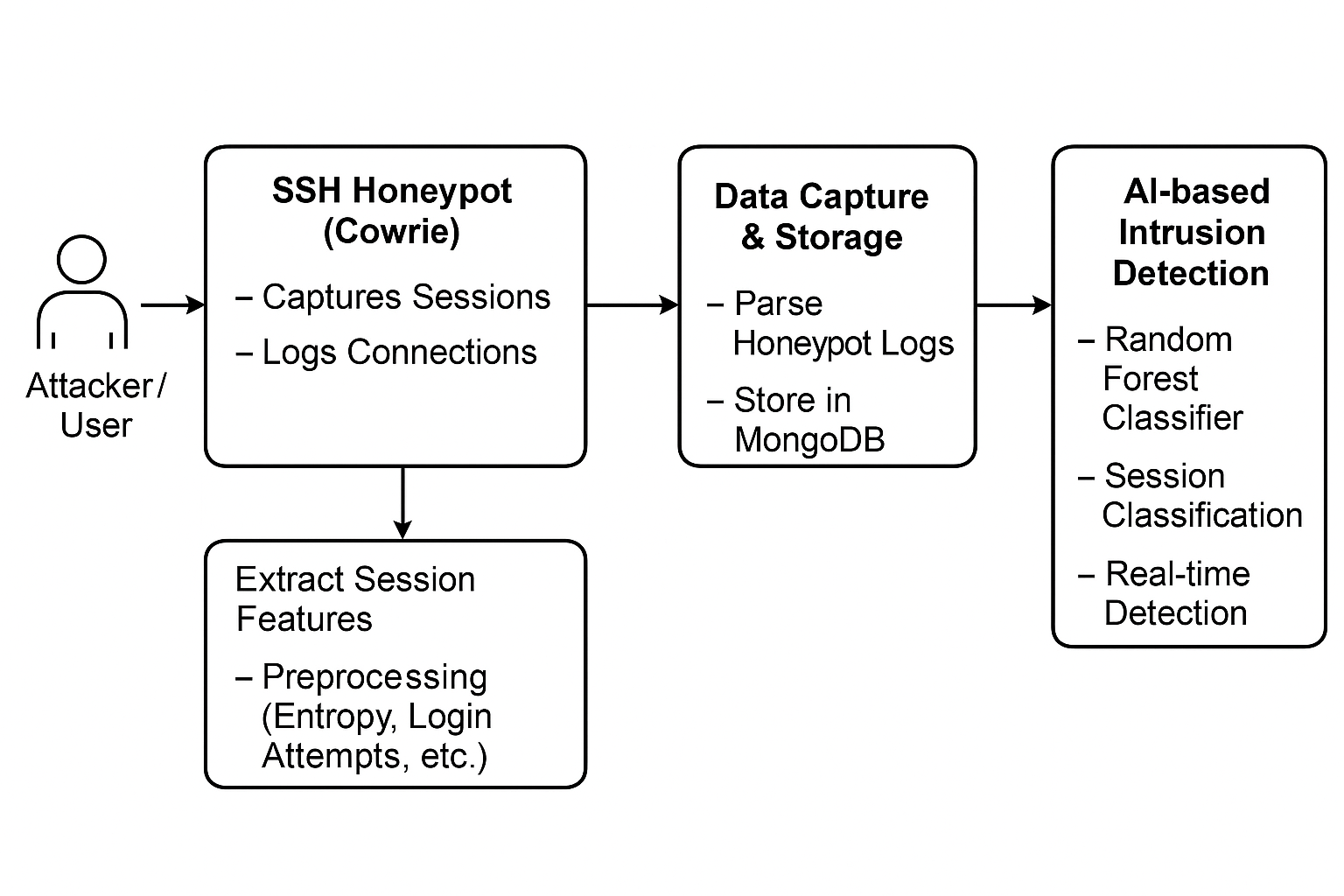
With the deep integration of artificial intelligence (AI) and Internet of Things (IoT) technologies, the maritime transportation industry is undergoing profound changes, and the application scenarios of unmanned surface vehicles (USVs) are constantly expanding. Aiming at the security threats faced by USV application systems, this paper proposes a new threat model for ship communication protocols and service logics, and the system covers the potential adversarial entity attack paths in application program logics and communication protocols. Based on this model, the automated security inspection framework USVScout was designed and implemented. By parsing the source code of the application prog... More >
Graphical Abstract