ICCK Transactions on Cybersecurity | Volume 1, Issue 2: 35-57, 2025-2026 | DOI: 10.62762/TC.2025.969565
Abstract
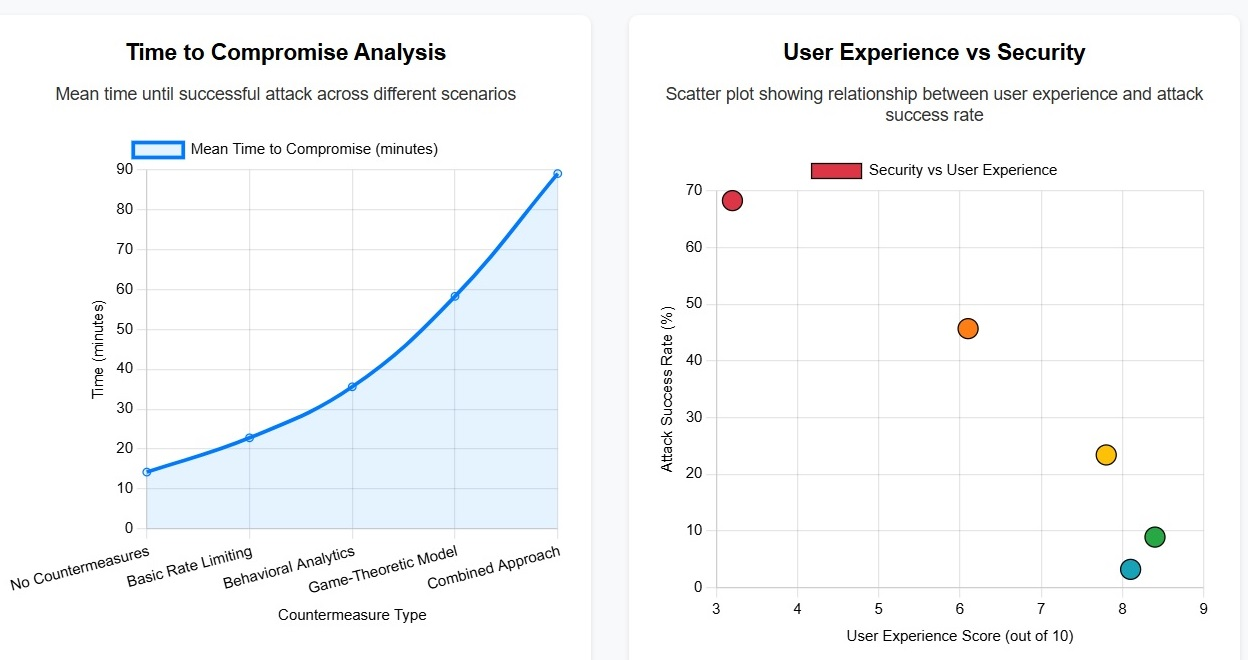
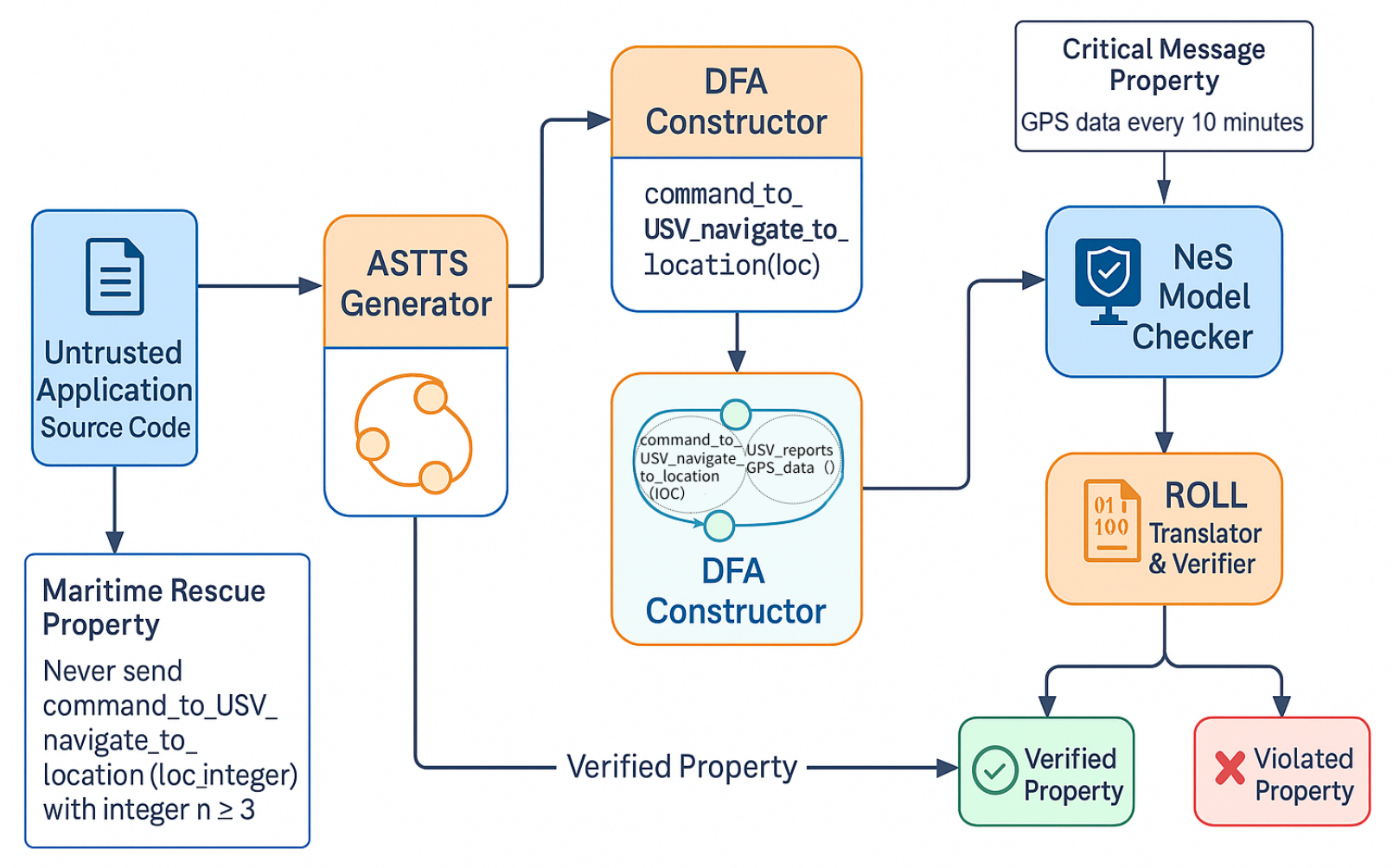
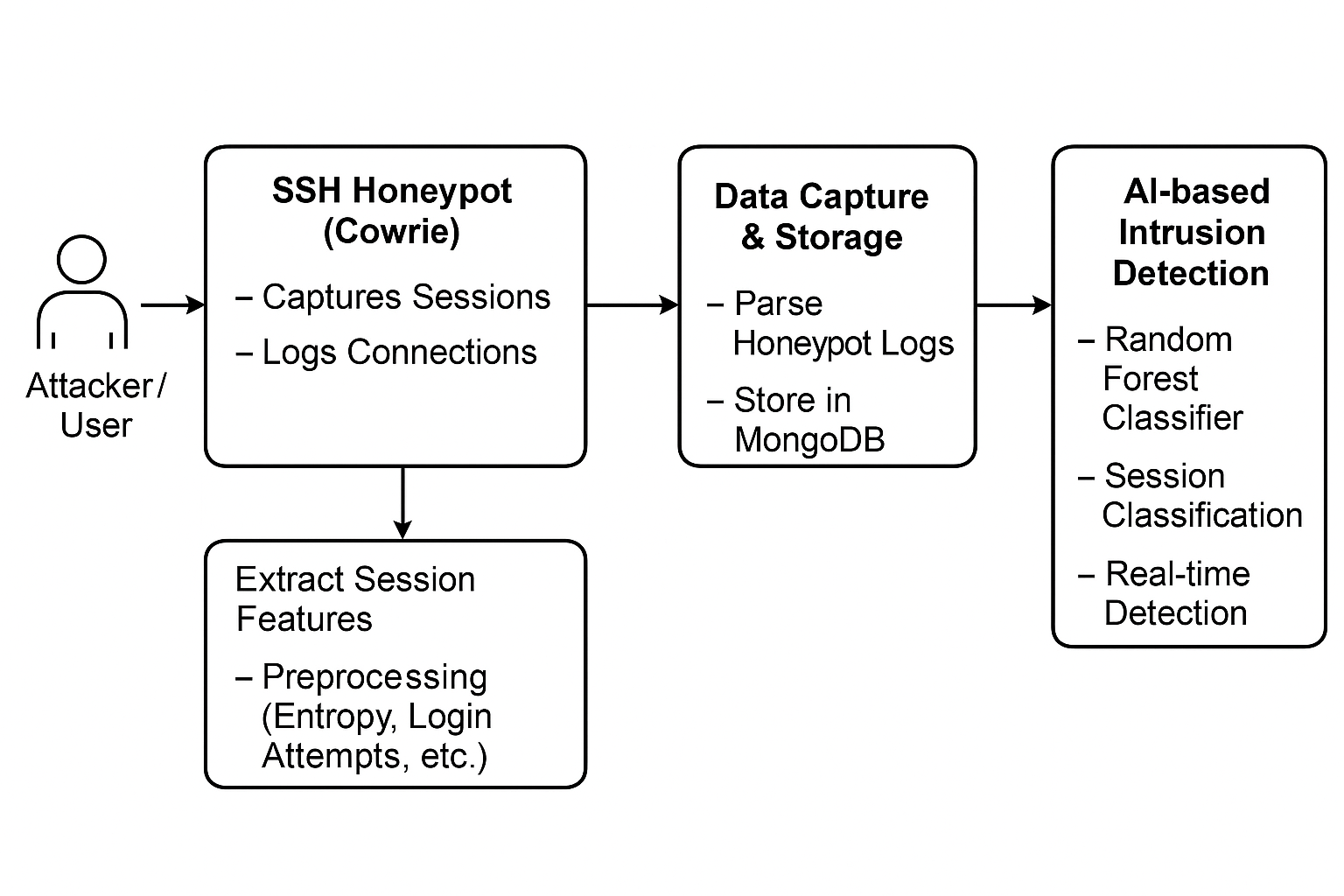
The rise of multi-factor authentication (MFA) has significantly enhanced cybersecurity postures, yet its effectiveness is increasingly challenged by sophisticated social engineering attacks, particularly those exploiting MFA fatigue. MFA fatigue, a tactic where attackers inundate users with authentication prompts, aims to induce erroneous approvals, as notably exemplified by the 2022 Uber breach. This phenomenon undermines the very security MFA is designed to provide by leveraging human vulnerabilities. Game theory, a powerful mathematical framework for analyzing strategic decision-making, offers a robust methodology to model the dynamic interactions between attackers and defenders. By apply... More >
Graphical Abstract