Abstract
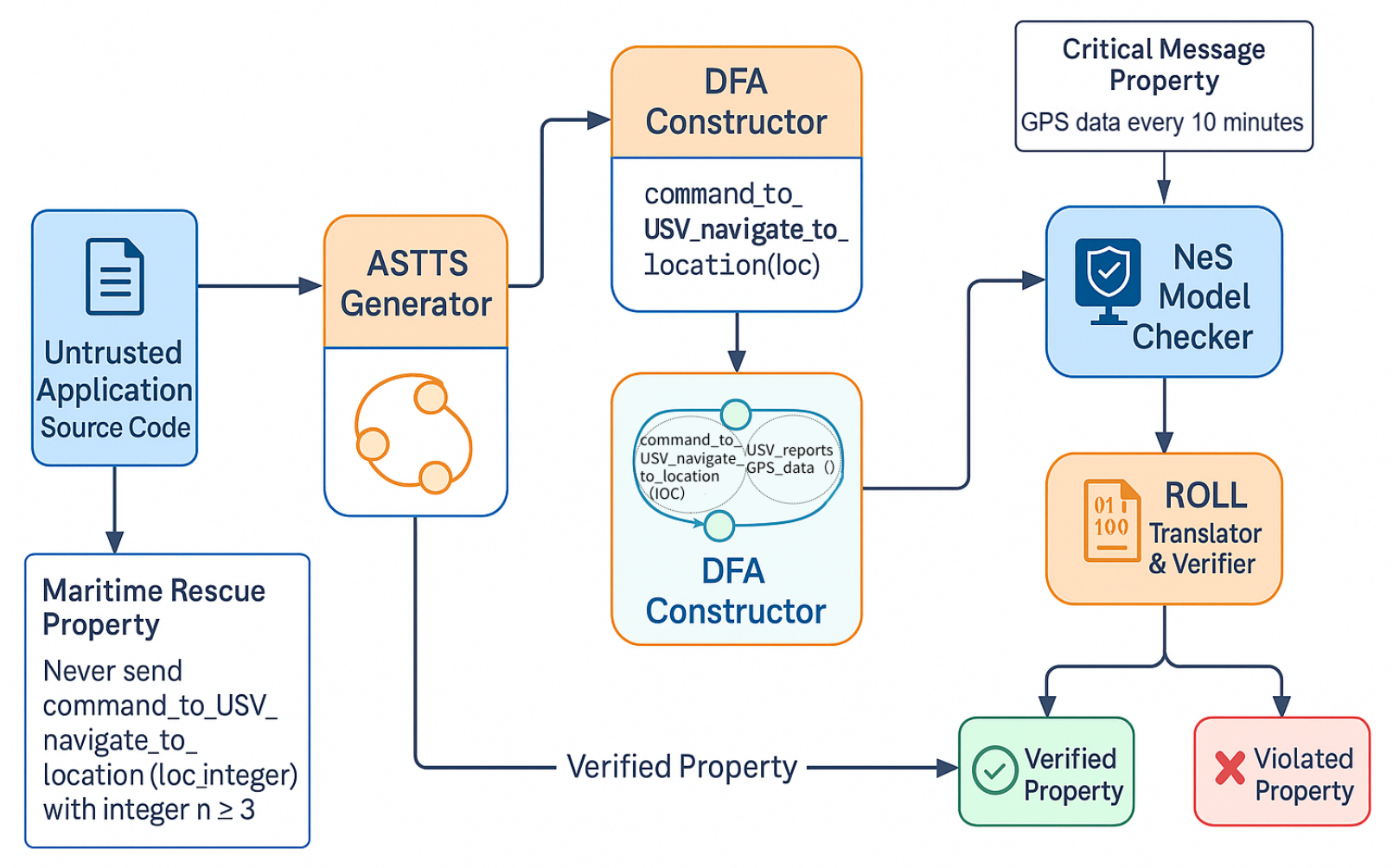
With the deep integration of artificial intelligence (AI) and Internet of Things (IoT) technologies, the maritime transportation industry is undergoing profound changes, and the application scenarios of unmanned surface vehicles (USVs) are constantly expanding. Aiming at the security threats faced by USV application systems, this paper proposes a new threat model for ship communication protocols and service logics, and the system covers the potential adversarial entity attack paths in application program logics and communication protocols. Based on this model, the automated security inspection framework USVScout was designed and implemented. By parsing the source code of the application program, the security analysis was formalized as an attribute verification task under the standard computing model, significantly improving the systematicness and accuracy of the detection. The experimental results show that in three real Marine application scenarios, USVScout successfully identified new types of vulnerabilities that static analysis tools failed to detect, and it can achieve sub-second real-time detection of 12 types of vulnerability patterns on an ordinary laptop, verifying the significant advantages of the method in terms of security and efficiency. The threat modeling and automated detection framework proposed in this paper provides technical support for ship network attack and defense drills and lays the foundation for building an intelligent and secure maritime transportation system.
Keywords
USVScout
threat modeling
automated security inspection
maritime transportation
Data Availability Statement
Data will be made available on request.
Funding
This work was supported without any funding.
Conflicts of Interest
Shihao Zhou is an employee of Three Gorges Navigation Authority, Yichang, China.
Ethical Approval and Consent to Participate
Not applicable.
Cite This Article
APA Style
Zhou, S. (2025). USVScout: Detecting Security Vulnerabilities in USV-based Marine Applications. ICCK Transactions on Cybersecurity, 1(1), 17–34. https://doi.org/10.62762/TC.2025.281528
Publisher's Note
ICCK stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and Permissions
Institute of Central Computation and Knowledge (ICCK) or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue