ICCK Transactions on Cybersecurity
ISSN: 3069-3349 (Online)
Email: [email protected]
 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
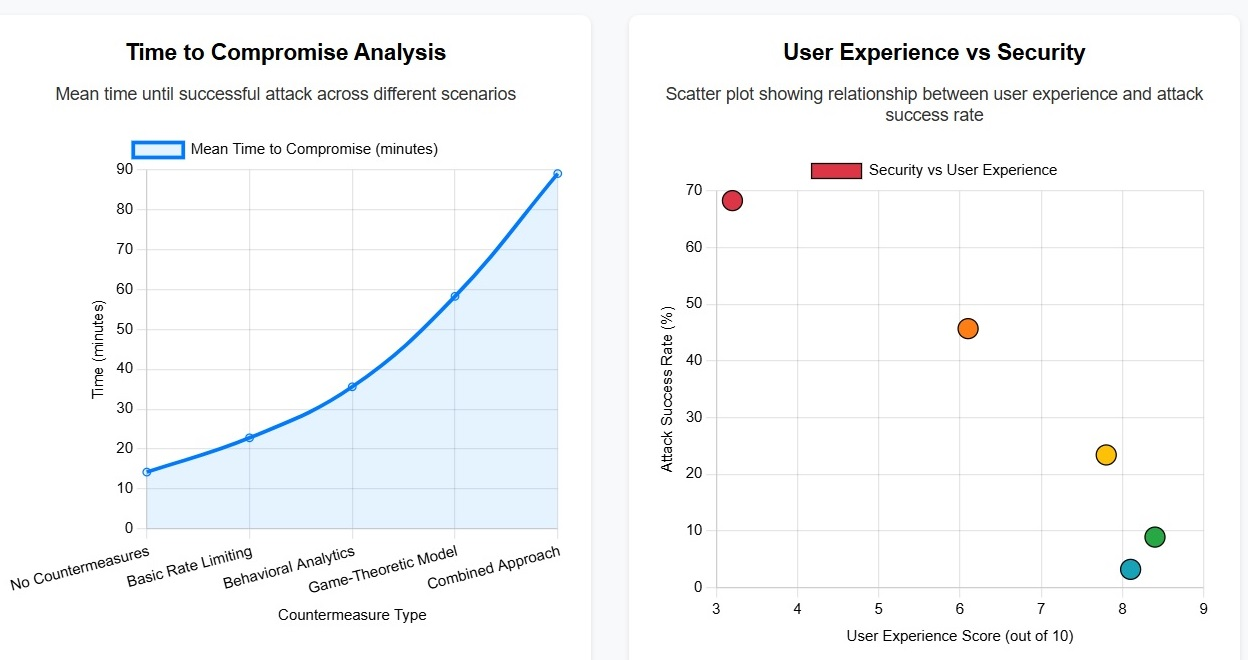
TY - JOUR AU - Vamsi, Tummalapalli Sri Ganesh AU - Yogi, Manas Kumar AU - Mundru, Yamuna PY - 2025 DA - 2025/12/25 TI - From Phishing to Prompt Bombing: Innovative Game-Theoretic Solutions for Modern Cyber Threats JO - ICCK Transactions on Cybersecurity T2 - ICCK Transactions on Cybersecurity JF - ICCK Transactions on Cybersecurity VL - 1 IS - 2 SP - 35 EP - 57 DO - 10.62762/TC.2025.969565 UR - https://www.icck.org/article/abs/TC.2025.969565 KW - game theory KW - cybersecurity KW - social engineering KW - MFA fatigue KW - multi-factor authentication KW - strategic interaction KW - behavioral security KW - nash equilibrium KW - empirical validation AB - The rise of multi-factor authentication (MFA) has significantly enhanced cybersecurity postures, yet its effectiveness is increasingly challenged by sophisticated social engineering attacks, particularly those exploiting MFA fatigue. MFA fatigue, a tactic where attackers inundate users with authentication prompts, aims to induce erroneous approvals, as notably exemplified by the 2022 Uber breach. This phenomenon undermines the very security MFA is designed to provide by leveraging human vulnerabilities. Game theory, a powerful mathematical framework for analyzing strategic decision-making, offers a robust methodology to model the dynamic interactions between attackers and defenders. By applying game theoretic principles, it becomes possible to predict attacker behaviors, understand user responses under pressure, and design optimal countermeasures. This article presents a comprehensive game-theoretic analysis of MFA fatigue attacks, including formal mathematical models, empirical validation through Monte Carlo simulations, and practical implementation frameworks. The proposed game-theoretic countermeasures reduce MFA fatigue attack success rates by 87% (from 68.3% to 8.9%) in simulations, with combined approaches achieving as low as 3.2% (=95% reduction) in some scenarios. The research synthesizes current approaches, provides novel theoretical contributions, and establishes a roadmap for future research in this critical cybersecurity domain. SN - 3069-3349 PB - Institute of Central Computation and Knowledge LA - English ER -
@article{Vamsi2025From,
author = {Tummalapalli Sri Ganesh Vamsi and Manas Kumar Yogi and Yamuna Mundru},
title = {From Phishing to Prompt Bombing: Innovative Game-Theoretic Solutions for Modern Cyber Threats},
journal = {ICCK Transactions on Cybersecurity},
year = {2025},
volume = {1},
number = {2},
pages = {35-57},
doi = {10.62762/TC.2025.969565},
url = {https://www.icck.org/article/abs/TC.2025.969565},
abstract = {The rise of multi-factor authentication (MFA) has significantly enhanced cybersecurity postures, yet its effectiveness is increasingly challenged by sophisticated social engineering attacks, particularly those exploiting MFA fatigue. MFA fatigue, a tactic where attackers inundate users with authentication prompts, aims to induce erroneous approvals, as notably exemplified by the 2022 Uber breach. This phenomenon undermines the very security MFA is designed to provide by leveraging human vulnerabilities. Game theory, a powerful mathematical framework for analyzing strategic decision-making, offers a robust methodology to model the dynamic interactions between attackers and defenders. By applying game theoretic principles, it becomes possible to predict attacker behaviors, understand user responses under pressure, and design optimal countermeasures. This article presents a comprehensive game-theoretic analysis of MFA fatigue attacks, including formal mathematical models, empirical validation through Monte Carlo simulations, and practical implementation frameworks. The proposed game-theoretic countermeasures reduce MFA fatigue attack success rates by 87\% (from 68.3\% to 8.9\%) in simulations, with combined approaches achieving as low as 3.2\% (=95\% reduction) in some scenarios. The research synthesizes current approaches, provides novel theoretical contributions, and establishes a roadmap for future research in this critical cybersecurity domain.},
keywords = {game theory, cybersecurity, social engineering, MFA fatigue, multi-factor authentication, strategic interaction, behavioral security, nash equilibrium, empirical validation},
issn = {3069-3349},
publisher = {Institute of Central Computation and Knowledge}
}

Portico
All published articles are preserved here permanently:
https://www.portico.org/publishers/icck/