ICCK Transactions on Information Security and Cryptography | Volume 1, Issue 1: 38-53, 2025 | DOI: 10.62762/TISC.2025.186894
Abstract
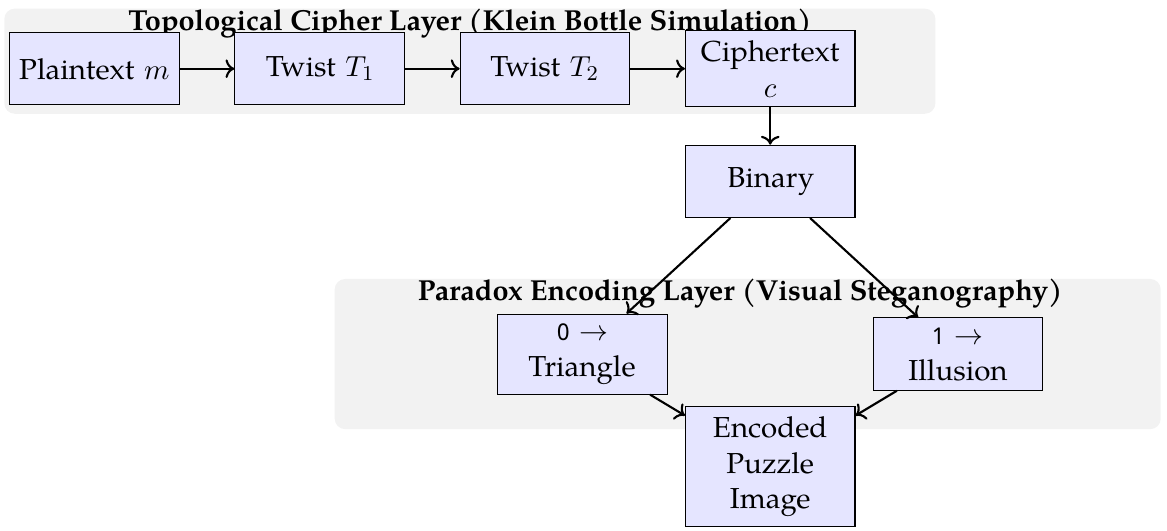
This paper presents the Singularity Cipher, a novel cryptographic-steganographic framework that integrates topological transformations and visual paradoxes to achieve multidimensional security. Inspired by the non-orientable properties of the Klein bottle—constructed from two Möbius strips—the cipher applies symbolic twist functions to simulate topological traversal, producing high confusion and diffusion in the ciphertext. The resulting binary data is then encoded using perceptual illusions, such as the missing square paradox, to visually obscure the presence of encrypted content. Unlike conventional ciphers that rely solely on algebraic complexity, the Singularity Cipher introduces a... More >
Graphical Abstract