Abstract
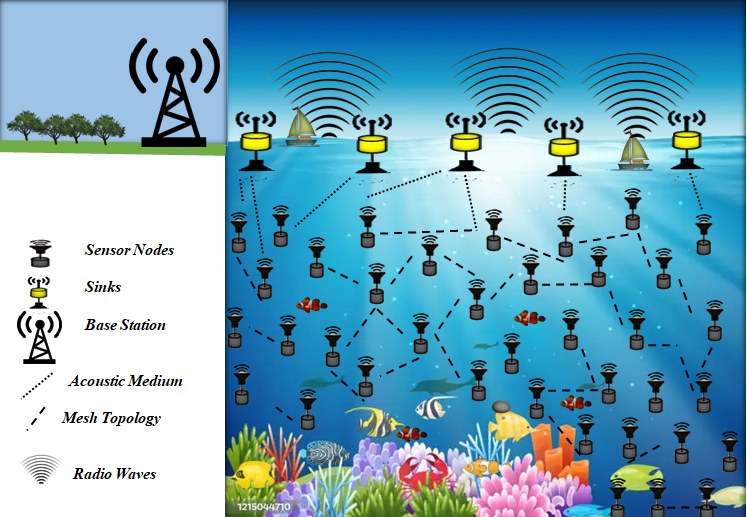
The emerging field of underwater sensor networks (UWSN) has a vital potential shaping the modern and future landscape that assists in measuring water quality, pollution tracking, and identification of underwater habitats. The challenging conditions in the UWSN environments raise data and security concerns in terms of outliers related to the complicated communication system, poor visibility, and limited resources. The data quality and network efficiency may be affected due to these unwanted conditions, giving rise to certain malicious activities in the network. This study aims to enhance the outlier identification process in terms of security and quality perspectives using the Long Short-Term Memory (LSTM) framework. The focus is to identify the temporal patterns and differentiate between various outliers in critical UWSN conditions. Results reveal that the proposed framework achieved high accuracy up to 95% and surpassed the other traditional machine learning models. It is worth mentioning that underwater sensor data have a complicated pattern that can be more appropriately handled using deep learning models, including LSTM, in comparison to traditional machine learning models.
Keywords
underwater sensor networks (UWSN)
anomaly detection (AD)
outlier detection (OD)
deep learning (DL)
long short-term memory (LSTM)
Data Availability Statement
Data will be made available on request.
Funding
This work was supported without any funding.
Conflicts of Interest
The authors declare no conflicts of interest.
Ethical Approval and Consent to Participate
Not applicable.
Cite This Article
APA Style
Rani, S., & Rahim, S. S. (2025). Secure Aware Outlier Detection in Underwater Wireless Sensor Networks using Deep Learning. ICCK Transactions on Information Security and Cryptography, 1(1), 25–37. https://doi.org/10.62762/TISC.2025.610386
Publisher's Note
ICCK stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and Permissions

Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (
https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
 Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.
Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. 