ICCK Transactions on Advanced Computing and Systems | Volume 1, Issue 4: 208-221, 2025 | DOI: 10.62762/TACS.2025.560376
Abstract
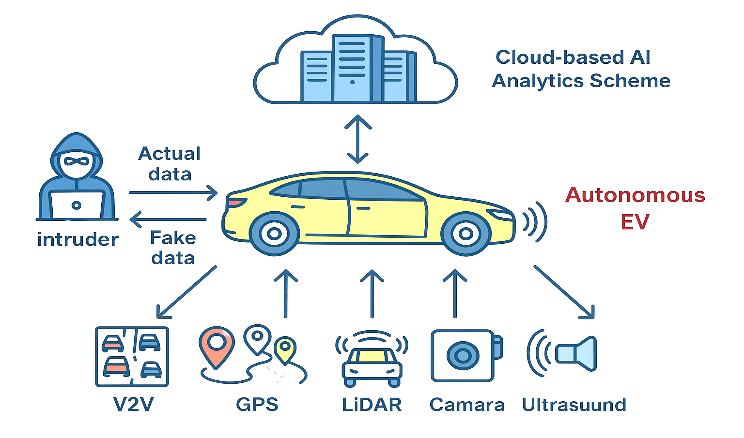
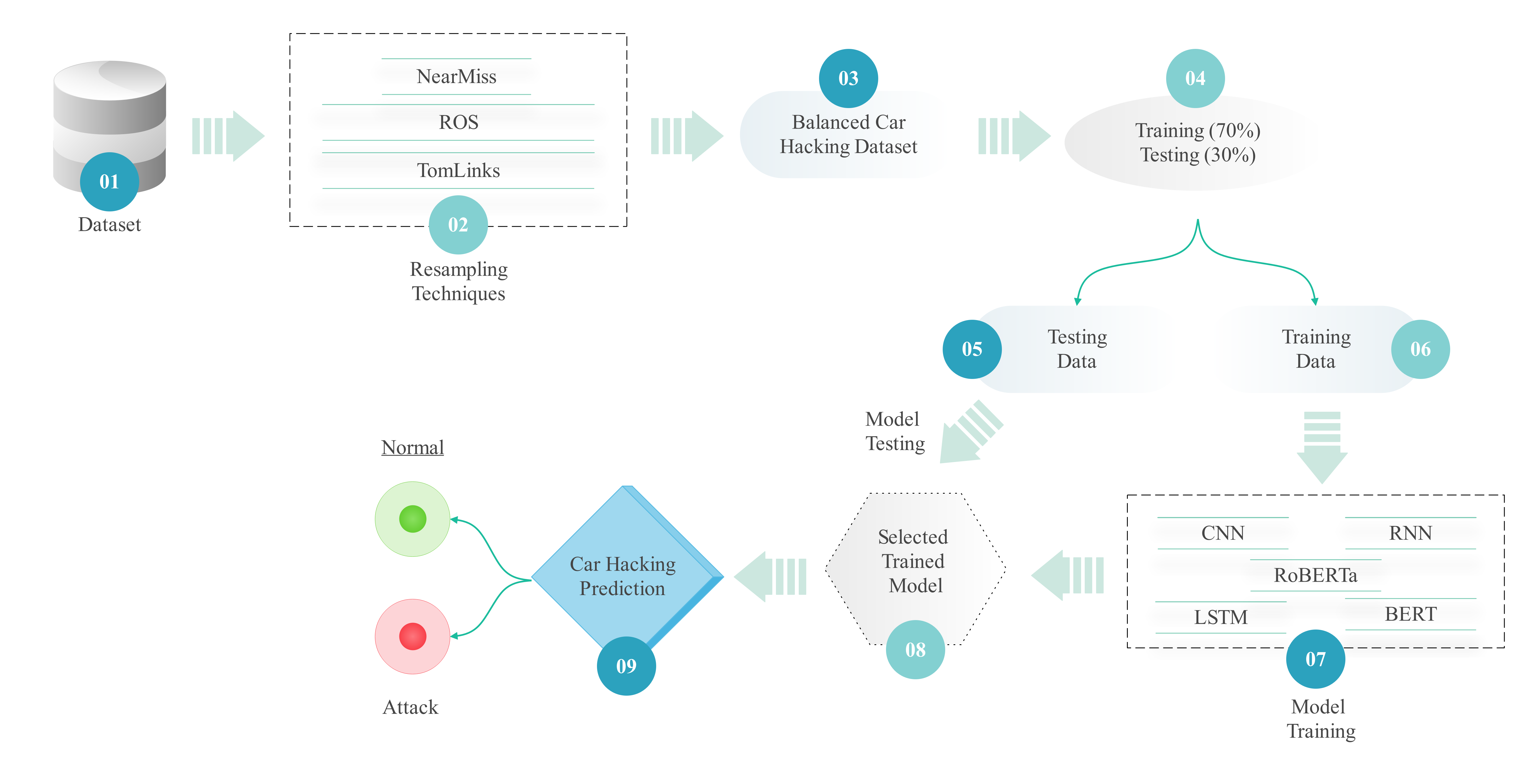
Real-time communication between autonomous vehicles, infrastructure, and their environment has facilitated the Internet of Vehicles (IoVs). Although this connectivity provides vehicular networks with significant benefits, it also introduces severe security threats, such as message injection attacks, particularly due to the heavy reliance on the Controller Area Network (CAN) protocol, which is inherently vulnerable. Electronic Control Units (ECUs) become primary targets for these attacks, leading to unsafe vehicle behaviors. To address these challenges, an Intrusion Detection System (IDS) based on deep learning architectures, Recurrent Neural Network (RNN), Long Short-Term Memory (LSTM), and... More >
Graphical Abstract