ICCK Journal of Software Engineering | Volume 1, Issue 1: 32-45, 2025 | DOI: 10.62762/JSE.2025.862549
Abstract
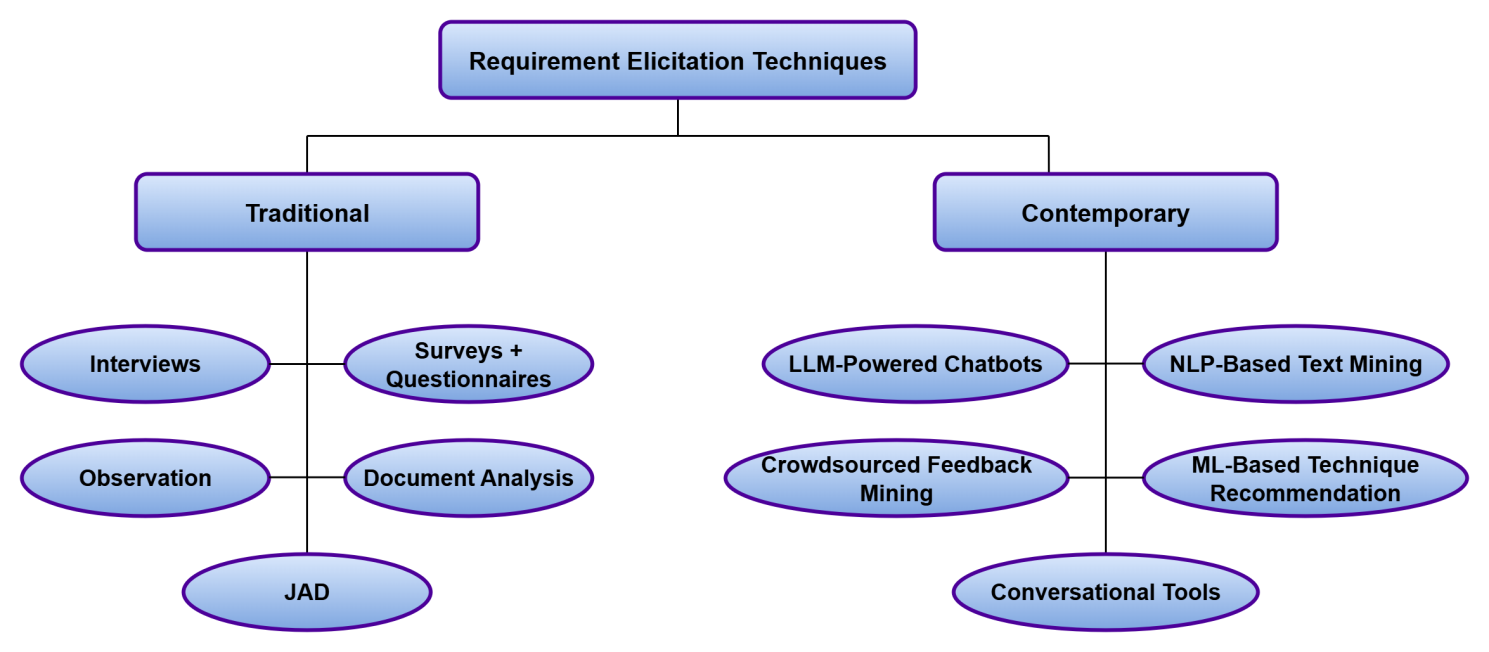
Requirements elicitation is one of the most important steps in the software development process. It involves understanding what users and stakeholders need from a system before it is built. Traditionally, this has been done using methods like interviews, questionnaires, document reviews, and direct observation. These approaches work well in structured environments but often fall short when dealing with large, fast-changing, or agile projects. In recent years, software development has shifted toward more flexible and fast-paced practices. This change has also affected how requirements are gathered. New techniques now include collaborative tools, user feedback from online platforms, and the us... More >
Graphical Abstract