ICCK Transactions on Information Security and Cryptography | Volume 2, Issue 1: 29-42, 2026 | DOI: 10.62762/TISC.2025.407888
Abstract
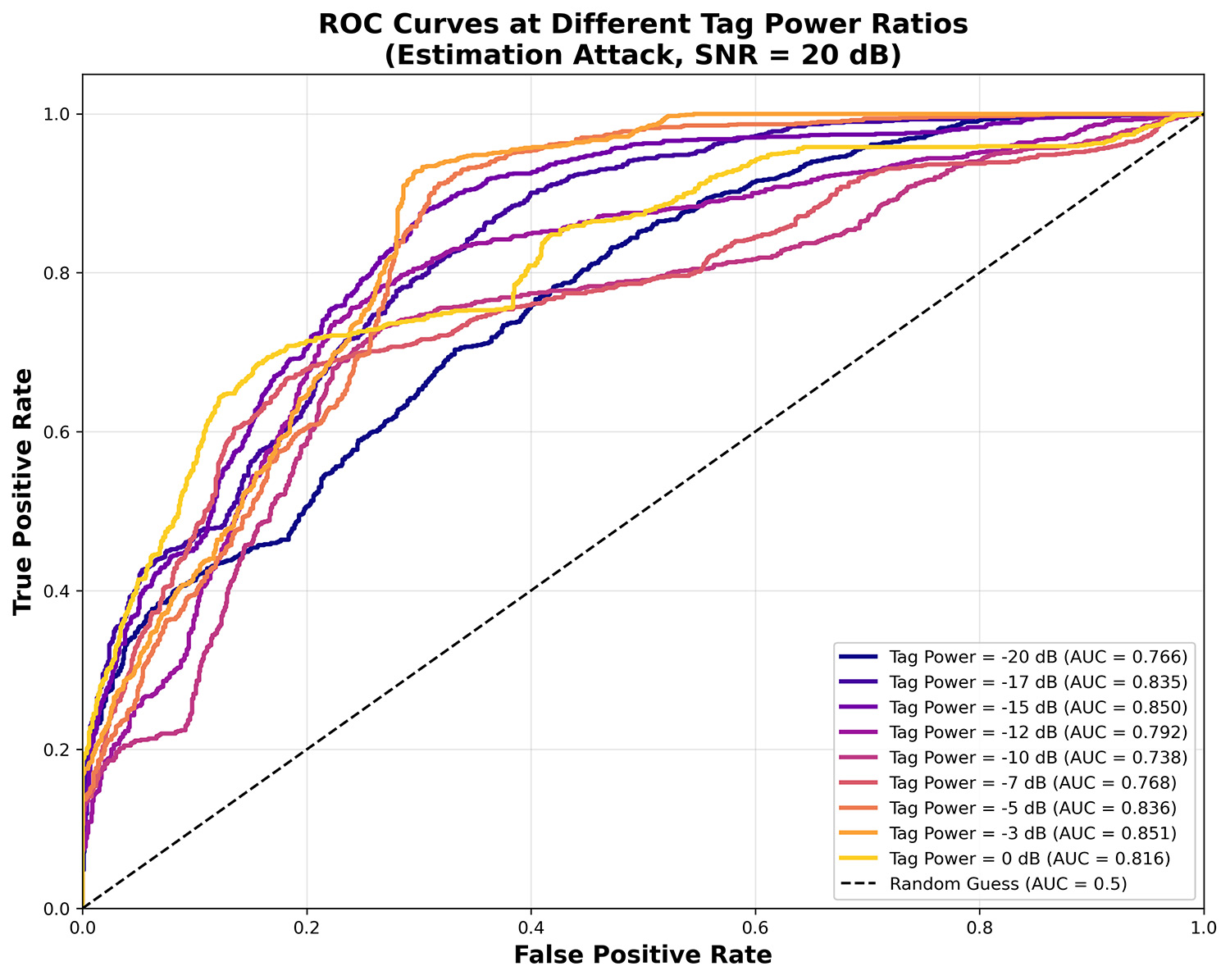
This paper investigates the performance of constellation warping techniques in QAM signals as a novel approach for physical layer authentication. We introduce a dynamic watermarking method that embeds subtle warping patterns into QAM constellations, enabling receivers to authenticate legitimate transmissions while detecting spoofing attacks. Our time-varying watermarking scheme employs secure key-based pattern generation to resist replay and estimation attacks. Extensive simulations analyze the system's resilience against various attack types (replay, blind spoofing, and estimation-based) across different signal-to-noise ratios. Results demonstrate that the proposed approach achieves high de... More >
Graphical Abstract