ICCK Transactions on Information Security and Cryptography
ISSN: 3070-2429 (Online)
Email: [email protected]
 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
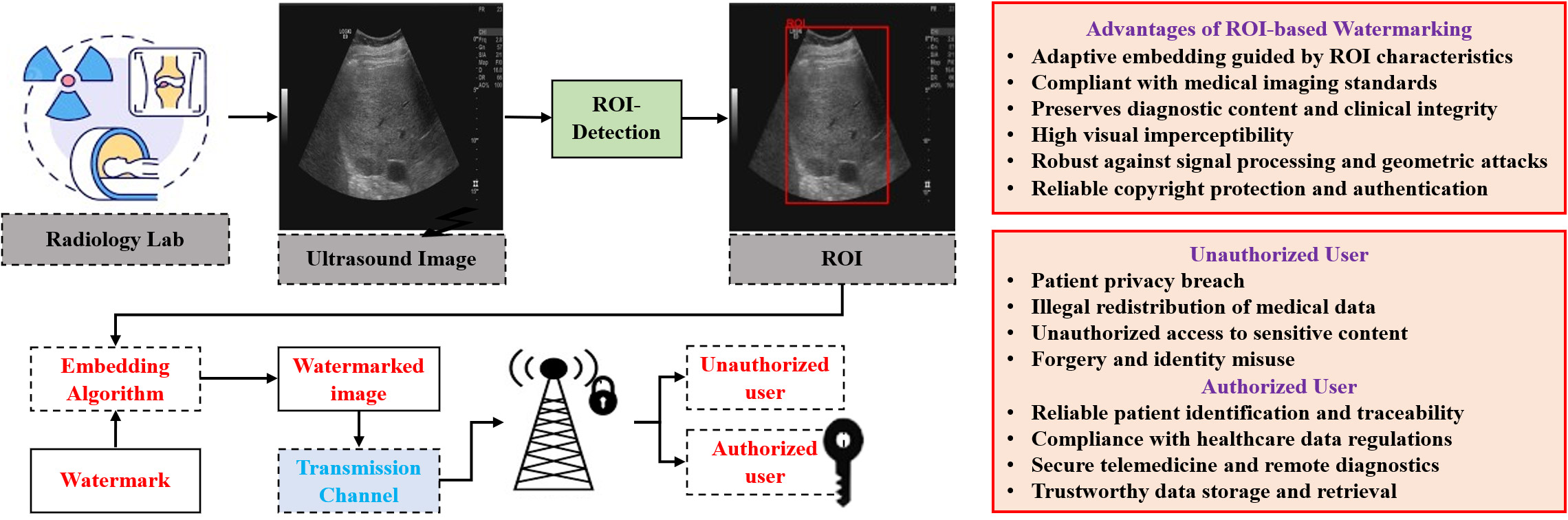
TY - JOUR AU - Awasthi, Divyanshu AU - Srivastava, Vinay Kumar PY - 2026 DA - 2026/02/10 TI - Optimized Copyright Protection of Scale-Adaptive Saliency-Driven ROI of Medical Records with MSER-Based authentication JO - ICCK Transactions on Information Security and Cryptography T2 - ICCK Transactions on Information Security and Cryptography JF - ICCK Transactions on Information Security and Cryptography VL - 2 IS - 1 SP - 43 EP - 54 DO - 10.62762/TISC.2025.898154 UR - https://www.icck.org/article/abs/TISC.2025.898154 KW - region of interest KW - watermarking KW - optimization KW - authentication AB - The medical information is always vulnerable to security violations. After the COVID-19 pandemic, the volume of medical information has exponentially increased and the major information is in the form of images. So, the security of this image information is crucial during the transfer using modern information and communication technologies from one place to another. Image watermarking is one of the methods to protect the copyright and integrity of medical records. The medical images consist of some area that has vital information regarding the disease and this area will be considered as the region of interest (ROI). Therefore, the protection of the copyright of this vital area is crucial for the effective diagnosis. The proposed technique utilizes a scale-adaptive anatomical saliency and a statistical information-guided ROI detection technique. The redundant wavelet transform (RDWT) and diagonalized Hessenberg decomposition (Diag-HD), along with the discrete cosine transform (DCT), are used for watermark embedding and extraction procedures. To get the optimized scaling weight, nature-inspired Salp Swarm Optimization (SSO) is used. Maximally stable extremal regions (MSER) are used for feature-based authentication. The simulation results analysis demonstrates the effectiveness in terms of visual similarity and robustness of the proposed technique. The experimental results obtained also highlight the superiority of the proposed technique over other existing methods in terms of imperceptibility and robustness. SN - 3070-2429 PB - Institute of Central Computation and Knowledge LA - English ER -
@article{Awasthi2026Optimized,
author = {Divyanshu Awasthi and Vinay Kumar Srivastava},
title = {Optimized Copyright Protection of Scale-Adaptive Saliency-Driven ROI of Medical Records with MSER-Based authentication},
journal = {ICCK Transactions on Information Security and Cryptography},
year = {2026},
volume = {2},
number = {1},
pages = {43-54},
doi = {10.62762/TISC.2025.898154},
url = {https://www.icck.org/article/abs/TISC.2025.898154},
abstract = {The medical information is always vulnerable to security violations. After the COVID-19 pandemic, the volume of medical information has exponentially increased and the major information is in the form of images. So, the security of this image information is crucial during the transfer using modern information and communication technologies from one place to another. Image watermarking is one of the methods to protect the copyright and integrity of medical records. The medical images consist of some area that has vital information regarding the disease and this area will be considered as the region of interest (ROI). Therefore, the protection of the copyright of this vital area is crucial for the effective diagnosis. The proposed technique utilizes a scale-adaptive anatomical saliency and a statistical information-guided ROI detection technique. The redundant wavelet transform (RDWT) and diagonalized Hessenberg decomposition (Diag-HD), along with the discrete cosine transform (DCT), are used for watermark embedding and extraction procedures. To get the optimized scaling weight, nature-inspired Salp Swarm Optimization (SSO) is used. Maximally stable extremal regions (MSER) are used for feature-based authentication. The simulation results analysis demonstrates the effectiveness in terms of visual similarity and robustness of the proposed technique. The experimental results obtained also highlight the superiority of the proposed technique over other existing methods in terms of imperceptibility and robustness.},
keywords = {region of interest, watermarking, optimization, authentication},
issn = {3070-2429},
publisher = {Institute of Central Computation and Knowledge}
}
ICCK Transactions on Information Security and Cryptography
ISSN: 3070-2429 (Online)
Email: [email protected]

Portico
All published articles are preserved here permanently:
https://www.portico.org/publishers/icck/