Abstract
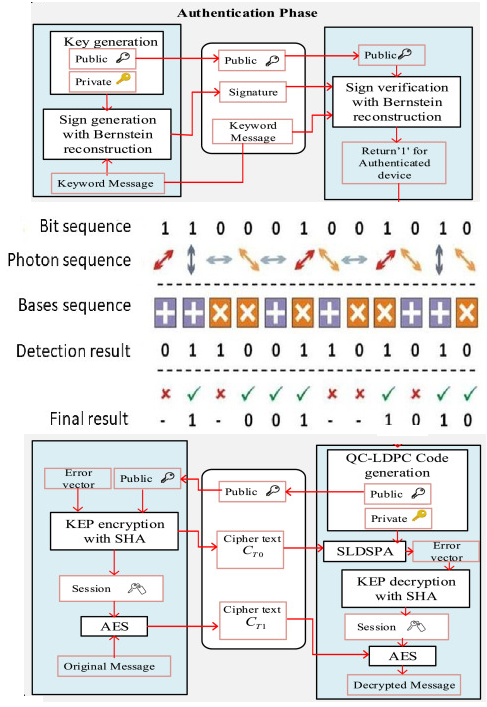
This research presents Quantum-Entangled Lattice-Augmented Cryptographic System (QELACS) a next-generation hybrid cryptographic framework that fuses quantum entanglement with algebraic lattice-based encryption to deliver quantum-safe, scalable, and high-performance data security. Unlike traditional hybrid models that merely layer quantum and classical methods, QELACS deeply integrates quantum mechanics into the cryptographic core, enabling entanglement-assisted operations across the encryption lifecycle. The framework introduces three foundational algorithms: Entanglement-Augmented Secret Key Generation (EASKG) for ultra-secure and rapid key production, Quantum-Lattice Encryption and Decryption (QLED) for post-quantum data confidentiality, and Quantum-Augmented Hybrid Authentication (QAHA) to establish resilient dual-layer authentication. These components jointly ensure end-to-end protection - confidentiality, integrity, and authenticity - against both classical and quantum adversaries. Analytical and experimental evaluations reveal that QELACS enhances key generation speed by 125%, reduces cryptographic latency by 59%, and minimizes security compromise risk to just 0.01%, significantly outperforming existing hybrid solutions. Designed for real-world adoption, QELACS is interoperable with current cryptographic infrastructures, tolerant to system noise, and compliant with NIST's post-quantum security guidelines. This work provides a strong foundation for secure communications in the quantum computing era, offering a transformative leap toward future-ready cryptographic ecosystems.
Keywords
quantum entanglement
lattice-based cryptography
post-quantum security
hybrid cryptosystems
quantum-classical authentication
QELACS
NIST compliance
Data Availability Statement
The datasets and codes used and/or analyzed in this study are available on GitHub: https://github.com/ankitkomar1/QELACS_Hybrid_Cryptography.
Funding
This work was supported and funded by the Deanship of Scientific Research at Imam Mohammad Ibn Saud Islamic University (IMSIU) under Grant IMSIU-DDRSP2504.
Conflicts of Interest
The authors declare no conflicts of interest.
Ethical Approval and Consent to Participate
Not applicable.
Cite This Article
APA Style
AlSagri, H. S., Kumar, A., Saudagar, A. K. J., Kumar, A., & Raja, L. (2025). Quantum-Algebraic Fusion: Hybrid Cryptographic Architectures for Post-Quantum Data Resilience. Journal of Quantum Cryptography, 1(1), 14–34. https://doi.org/10.62762/JQC.2025.497251
Publisher's Note
ICCK stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and Permissions

Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (
https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
 Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.
Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. 