Abstract
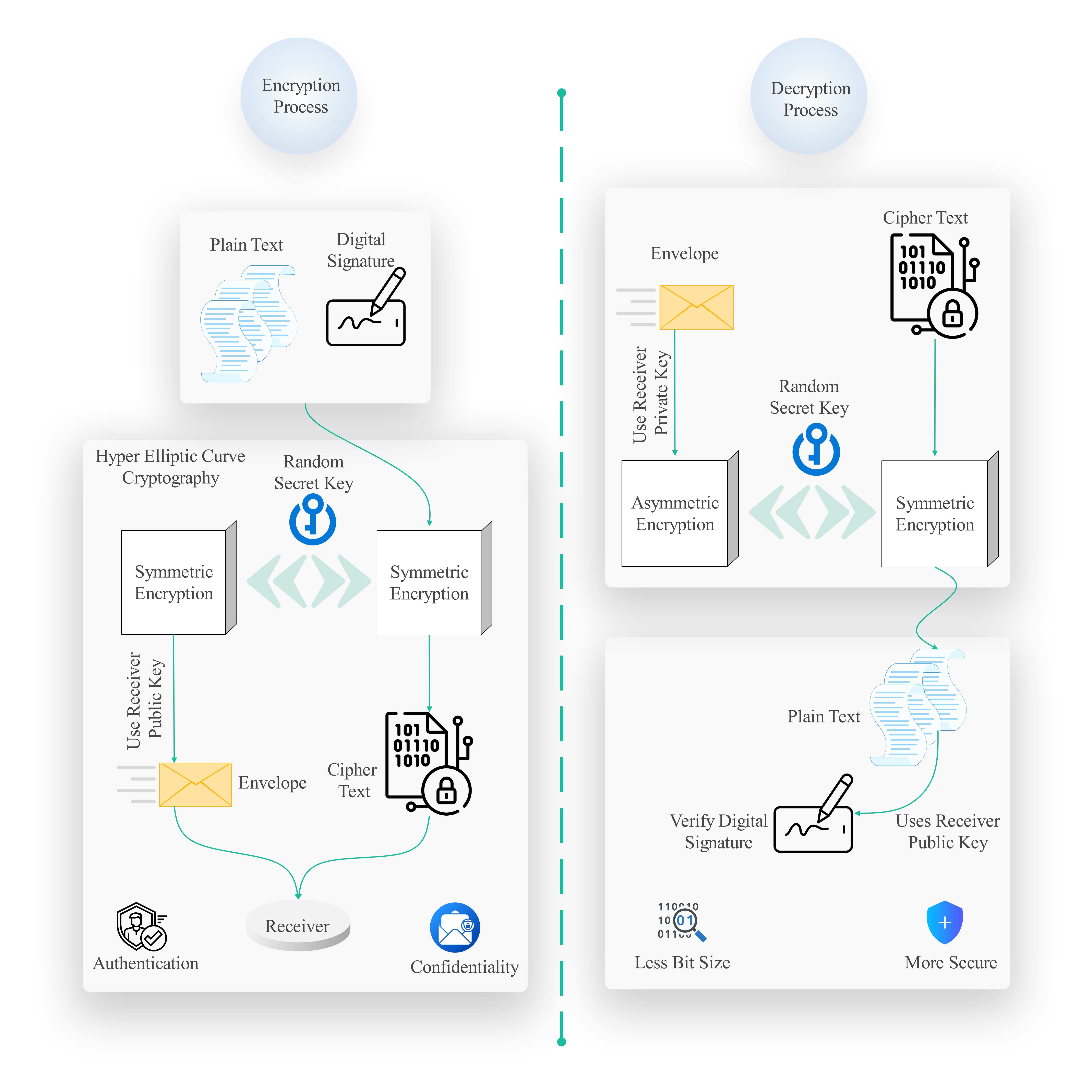
The concept of an Internet of Drones (IoD) is becoming increasingly important in various domains, including surveillance and logistics. Effective communication between the interconnected systems is the essence of the Internet of Drones, however, due to the resource constraints of drones and the dynamic nature of the operating environment, security of communication within IoD networks is indeed the top priority. Considering these challenges on the part of IoD communication, a novel Hyperelliptic Curve Cryptography (HECC)-based authentication protocol is proposed in this paper to secure the data exchange between two drones and to ensure efficient communication. The proposed HECC protocol is compared with three existing protocols, Elliptic curve cryptography-based protocol with public secure authentication scheme (ECCCPSAS), Non-linear wireless unmanned aerial systems authentication scheme (NLWUAS), and the Multi-Agent System (MAS). The comparison is made among average performance metrics such as communication overhead, packet delivery ratio, throughput, and end-to-end delay. The experimental outcome assures that the HECC protocol outperforms the other protocols in terms of all metrics. HECC provides Minimum communication overhead, Maximum packet delivery ratio, Maximum throughput, and Minimum end-to-end delay. The HECC-based authentication protocol enhances communication security in IoD networks by reducing computational overload as well as improving packet delivery, and is beneficial for resource-constrained environments like drones. This efficiency is particularly valuable in practical scenarios like autonomous fleets of drones for observation or delivery, as it reduces delays and energy use. It is suggested by the results of our study that, for drone communication in IoD networks, HECC is a much more secure and scalable solution as compared to all other alternatives. Ongoing research will focus on the practical deployment of the protocol and support for future quantum-resistant algorithms.
Keywords
hyperelliptic curve cryptography
internet of drones (IoD)
authentication protocol
cryptographic protocols
drone communication networks
security in IoD
Data Availability Statement
Data will be made available on request.
Funding
This work was supported without any funding.
Conflicts of Interest
The authors declare no conflicts of interest.
Ethical Approval and Consent to Participate
Not applicable.
Cite This Article
APA Style
Haider, Z. A., Fayaz, M., Zhang, Y., & Ali, A. (2024). Advanced Hyperelliptic Curve-Based Authentication Protocols for Secure Internet of Drones Communication. ICCK Transactions on Advanced Computing and Systems, 1(4), 1–16. https://doi.org/10.62762/TACS.2024.926789
Publisher's Note
ICCK stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and Permissions

Copyright © 2024 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (
https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
 Copyright © 2024 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.
Copyright © 2024 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. 
