Abstract
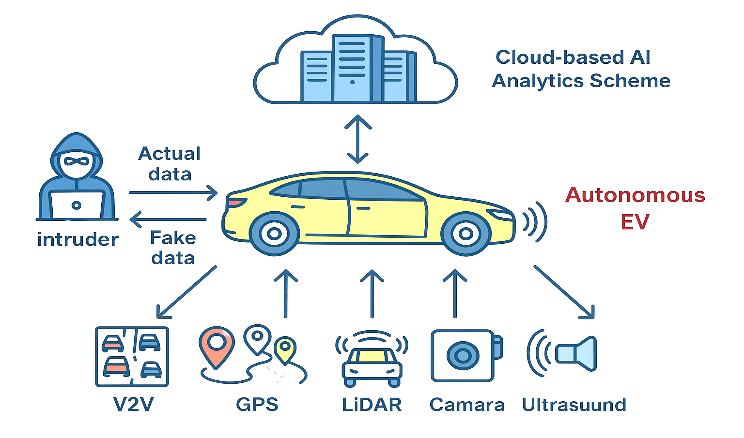
Real-time communication between autonomous vehicles, infrastructure, and their environment has facilitated the Internet of Vehicles (IoVs). Although this connectivity provides vehicular networks with significant benefits, it also introduces severe security threats, such as message injection attacks, particularly due to the heavy reliance on the Controller Area Network (CAN) protocol, which is inherently vulnerable. Electronic Control Units (ECUs) become primary targets for these attacks, leading to unsafe vehicle behaviors. To address these challenges, an Intrusion Detection System (IDS) based on deep learning architectures, Recurrent Neural Network (RNN), Long Short-Term Memory (LSTM), and Gated Recurrent Unit (GRU) is proposed for detecting and classifying cyberattacks in vehicular networks. Data preprocessing techniques such as NearMiss, Random Over-Sampling (ROS), and Tomek Links are applied to handle class imbalance in the car hacking dataset. A benchmark Car-Hacking dataset, evaluation metrics including accuracy, precision, recall, and F1 score, are used to assess the performance of the models. The experimental results demonstrate that the GRU model achieves the highest accuracy of 99%, followed by LSTM with 98%, and RNN with 94%. These findings indicate that GRU outperforms the other models and, in certain configurations, detects 100% of the attacks. The proposed IDS exhibits considerable superiority over traditional deep learning approaches, presenting a promising and intelligent solution for enhancing the cybersecurity of modern IoV systems.
Keywords
internet of vehicles
car hacking
random over-sampling (Ros)
nearmiss
imbalanced data
intrusion detection systems
deep learning
Data Availability Statement
Data will be made available on request.
Funding
This work was supported without any funding.
Conflicts of Interest
The authors declare no conflicts of interest.
Ethical Approval and Consent to Participate
Not applicable.
Cite This Article
APA Style
Nawaz, M. H., Ahsan, A., Khan, I. U., Wang, Y., Ahmad, M., & Akhtar, M. S. (2025). Mitigating Message Injection Attacks in Internet of Vehicles Using Deep Learning Based Intrusion Detection System. ICCK Transactions on Advanced Computing and Systems, 1(4), 208–221. https://doi.org/10.62762/TACS.2025.560376
Publisher's Note
ICCK stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and Permissions

Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (
https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
 Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.
Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. 
