Journal of Reliable and Secure Computing
ISSN: 3070-6424 (Online)
Email: [email protected]
 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
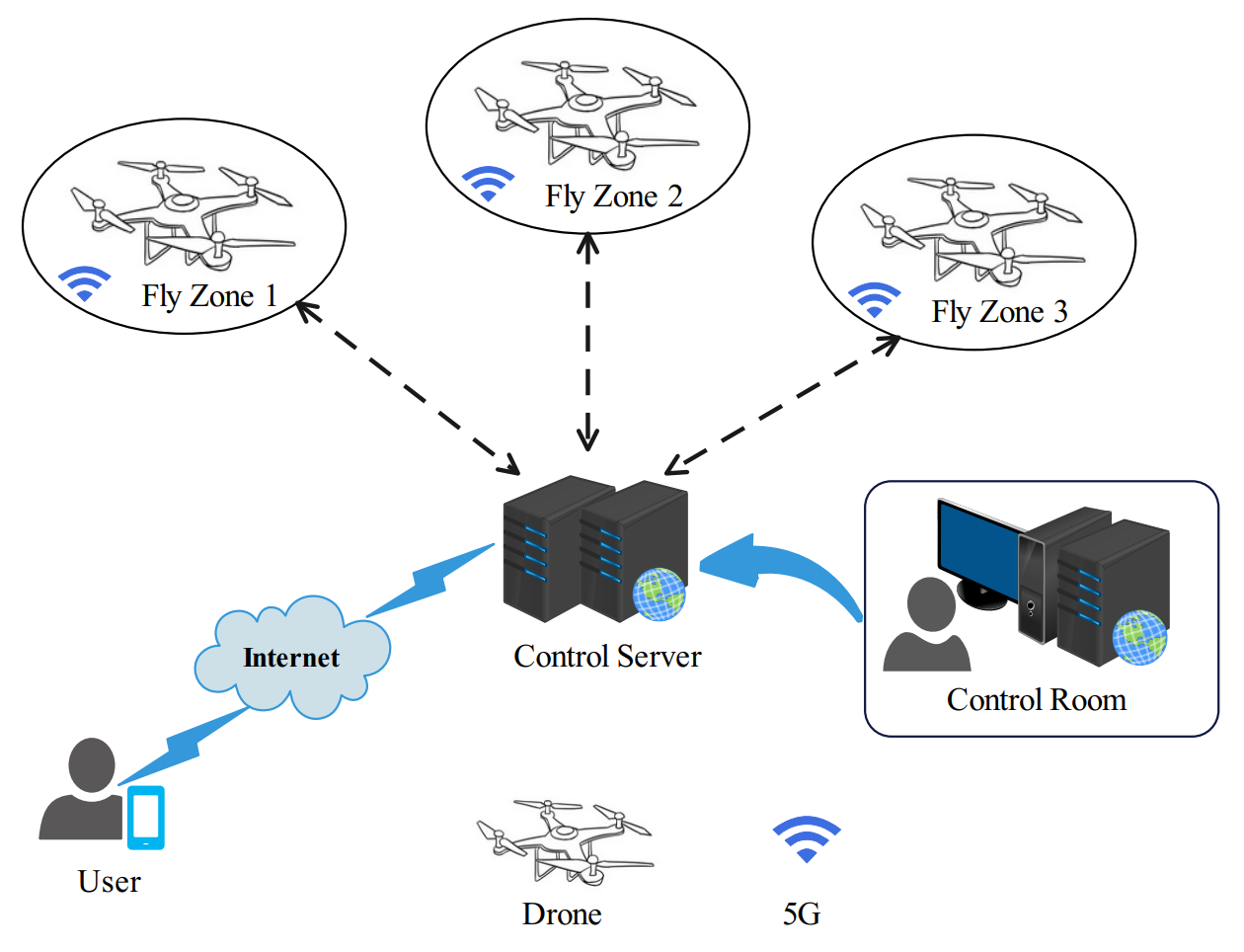
TY - JOUR AU - Tang, Maoxin AU - Li, Haonan PY - 2025 DA - 2025/12/19 TI - PUF-AKA-IoD: A Provably Secure PUF-Based Authentication and Key Agreement Protocol for IoD over 5G Networks JO - Journal of Reliable and Secure Computing T2 - Journal of Reliable and Secure Computing JF - Journal of Reliable and Secure Computing VL - 1 IS - 1 SP - 25 EP - 40 DO - 10.62762/JRSC.2025.869145 UR - https://www.icck.org/article/abs/JRSC.2025.869145 KW - IoD KW - 5G networks KW - mutual authentication KW - key agreement KW - PUF AB - The Internet of Things (IoT) is a technological ecosystem that interconnects physical devices via the Internet to enable data exchange and coordinated operations, among which the Internet of Drones (IoD) represents a specialized application integrating drone technology with IoT for remote control and data transmission. With the adoption of fifth-generation (5G) mobile communication networks in IoD environments, drones can transmit high-quality data and respond to user requests with reduced latency. In recent years, various authentication schemes using temporary credentials have been proposed to allow users and drones to establish session keys with the assistance of a control server; however, many existing schemes remain vulnerable to drone capture attacks and known session-specific temporary information attacks. To address these security challenges, this paper proposes an enhanced authentication and key agreement scheme for IoD over 5G networks that incorporates physically unclonable functions (PUFs) to strengthen drone data security. The security of the proposed scheme is validated through informal security analysis, the ROR model, and the AVISPA tool. Furthermore, comparative security and performance evaluations demonstrate that the proposed scheme achieves adequate security while maintaining competitive performance relative to existing schemes. SN - 3070-6424 PB - Institute of Central Computation and Knowledge LA - English ER -
@article{Tang2025PUFAKAIoD,
author = {Maoxin Tang and Haonan Li},
title = {PUF-AKA-IoD: A Provably Secure PUF-Based Authentication and Key Agreement Protocol for IoD over 5G Networks},
journal = {Journal of Reliable and Secure Computing},
year = {2025},
volume = {1},
number = {1},
pages = {25-40},
doi = {10.62762/JRSC.2025.869145},
url = {https://www.icck.org/article/abs/JRSC.2025.869145},
abstract = {The Internet of Things (IoT) is a technological ecosystem that interconnects physical devices via the Internet to enable data exchange and coordinated operations, among which the Internet of Drones (IoD) represents a specialized application integrating drone technology with IoT for remote control and data transmission. With the adoption of fifth-generation (5G) mobile communication networks in IoD environments, drones can transmit high-quality data and respond to user requests with reduced latency. In recent years, various authentication schemes using temporary credentials have been proposed to allow users and drones to establish session keys with the assistance of a control server; however, many existing schemes remain vulnerable to drone capture attacks and known session-specific temporary information attacks. To address these security challenges, this paper proposes an enhanced authentication and key agreement scheme for IoD over 5G networks that incorporates physically unclonable functions (PUFs) to strengthen drone data security. The security of the proposed scheme is validated through informal security analysis, the ROR model, and the AVISPA tool. Furthermore, comparative security and performance evaluations demonstrate that the proposed scheme achieves adequate security while maintaining competitive performance relative to existing schemes.},
keywords = {IoD, 5G networks, mutual authentication, key agreement, PUF},
issn = {3070-6424},
publisher = {Institute of Central Computation and Knowledge}
}
 Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.
Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. 
Portico
All published articles are preserved here permanently:
https://www.portico.org/publishers/icck/