Journal of Reliable and Secure Computing | Volume 2, Issue 1: 1-26, 2026 | DOI: 10.62762/JRSC.2025.761390
Abstract
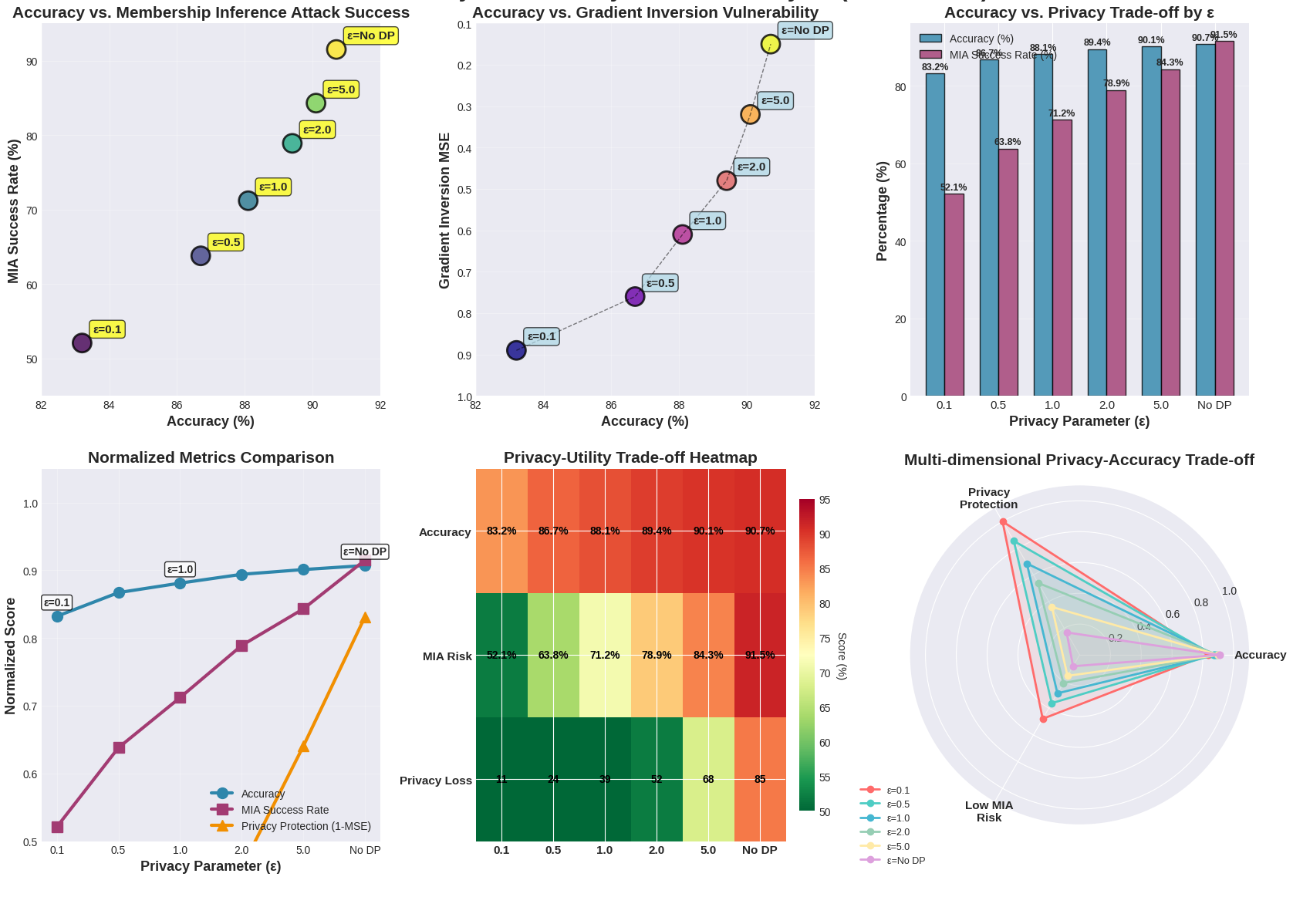
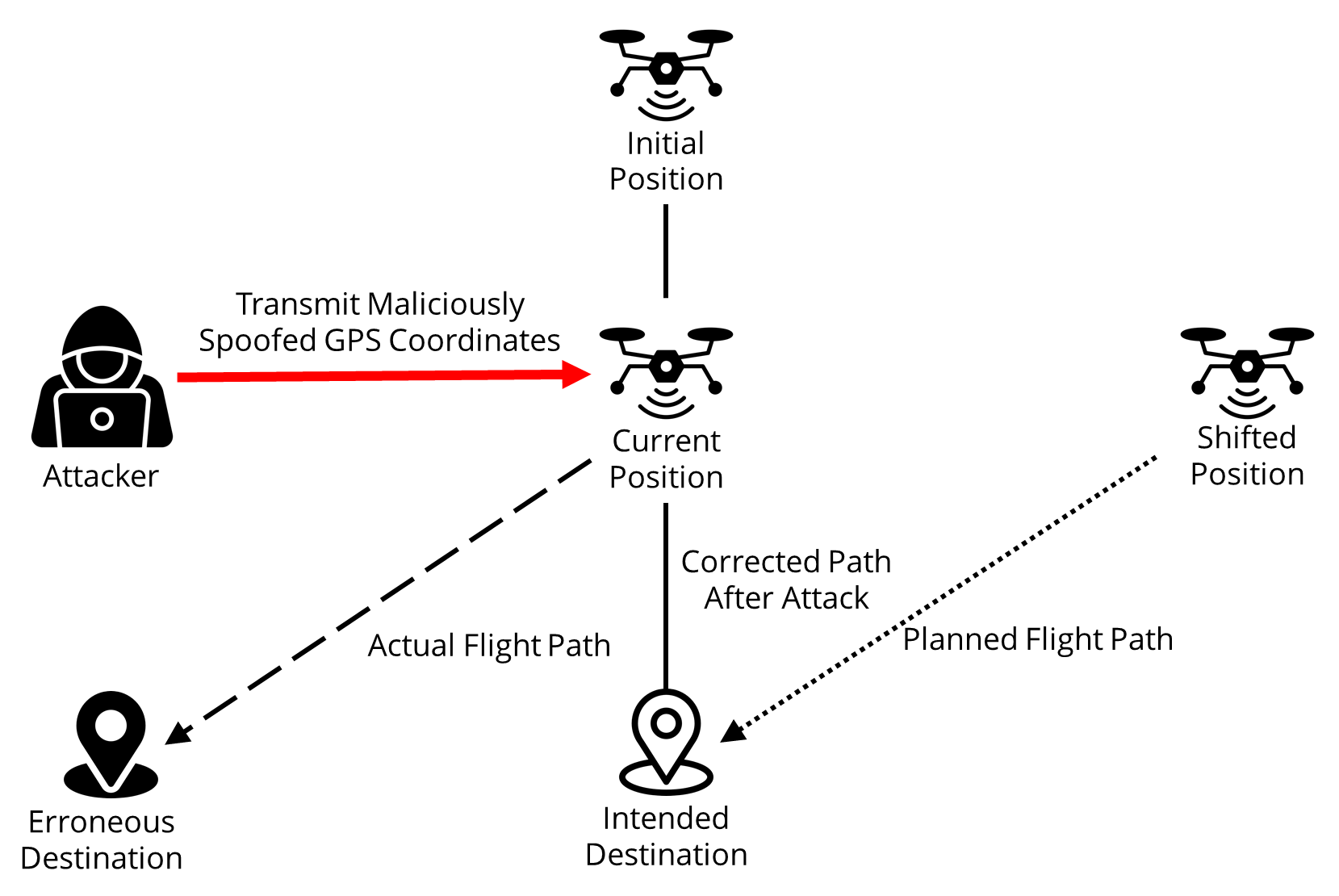
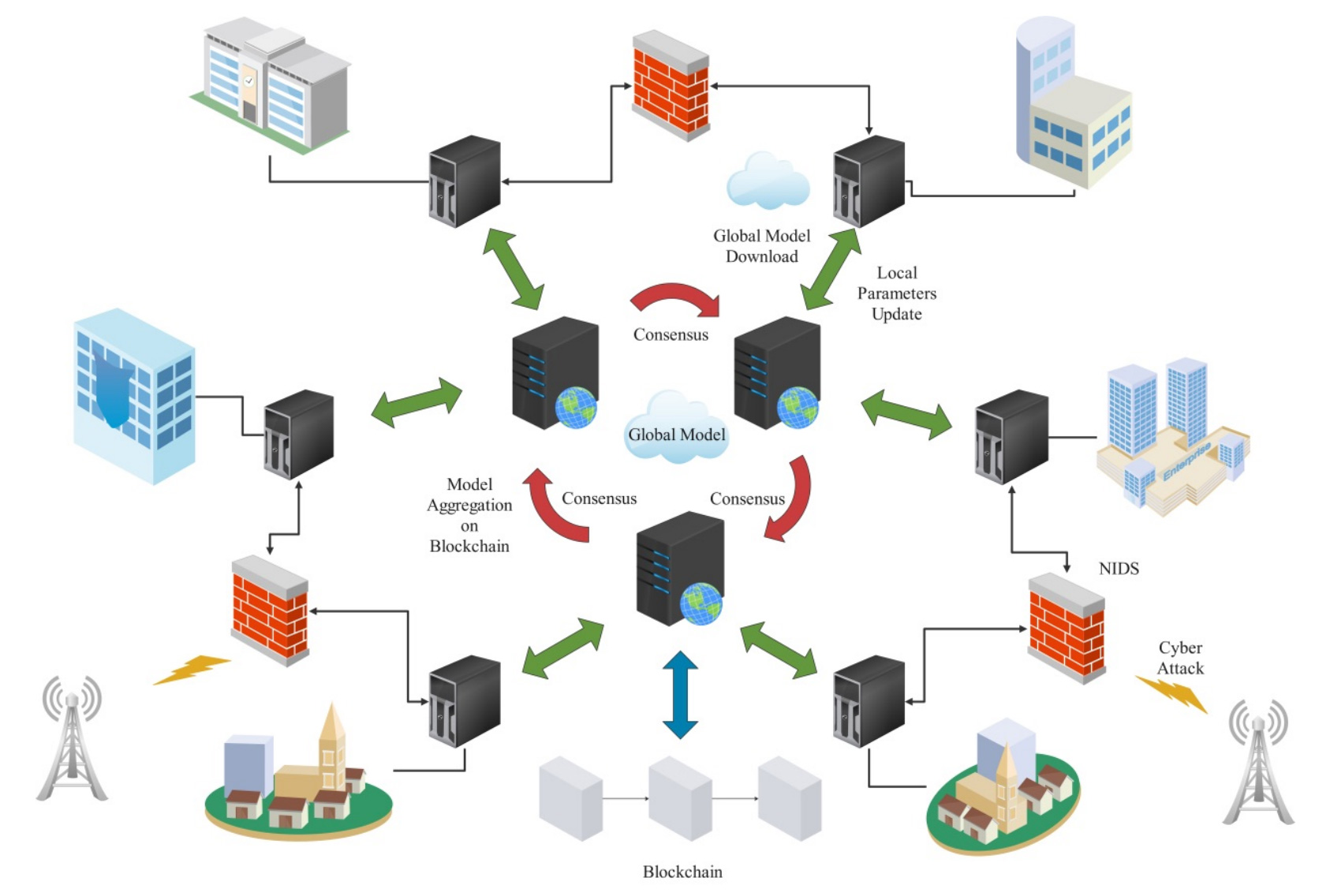
The rapid proliferation of smart home IoT devices has introduced unprecedented cybersecurity vulnerabilities, necessitating scalable and privacy-preserving intrusion detection systems (IDS). Federated Learning (FL) offers a promising decentralized approach by training models locally without sharing raw data, but it remains susceptible to poisoning attacks and relies on a vulnerable central aggregator. This paper presents a novel blockchain-enhanced FL framework tailored for smart home IDS, integrating multiple consensus mechanisms—Proof-of-Stake (PoS), Practical Byzantine Fault Tolerance (PBFT), and Proof-of-Authority (PoA)—for the first time in this context. Our approach uniquely combin... More >
Graphical Abstract