Journal of Reliable and Secure Computing
ISSN: 3070-6424 (Online)
Email: [email protected]
 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
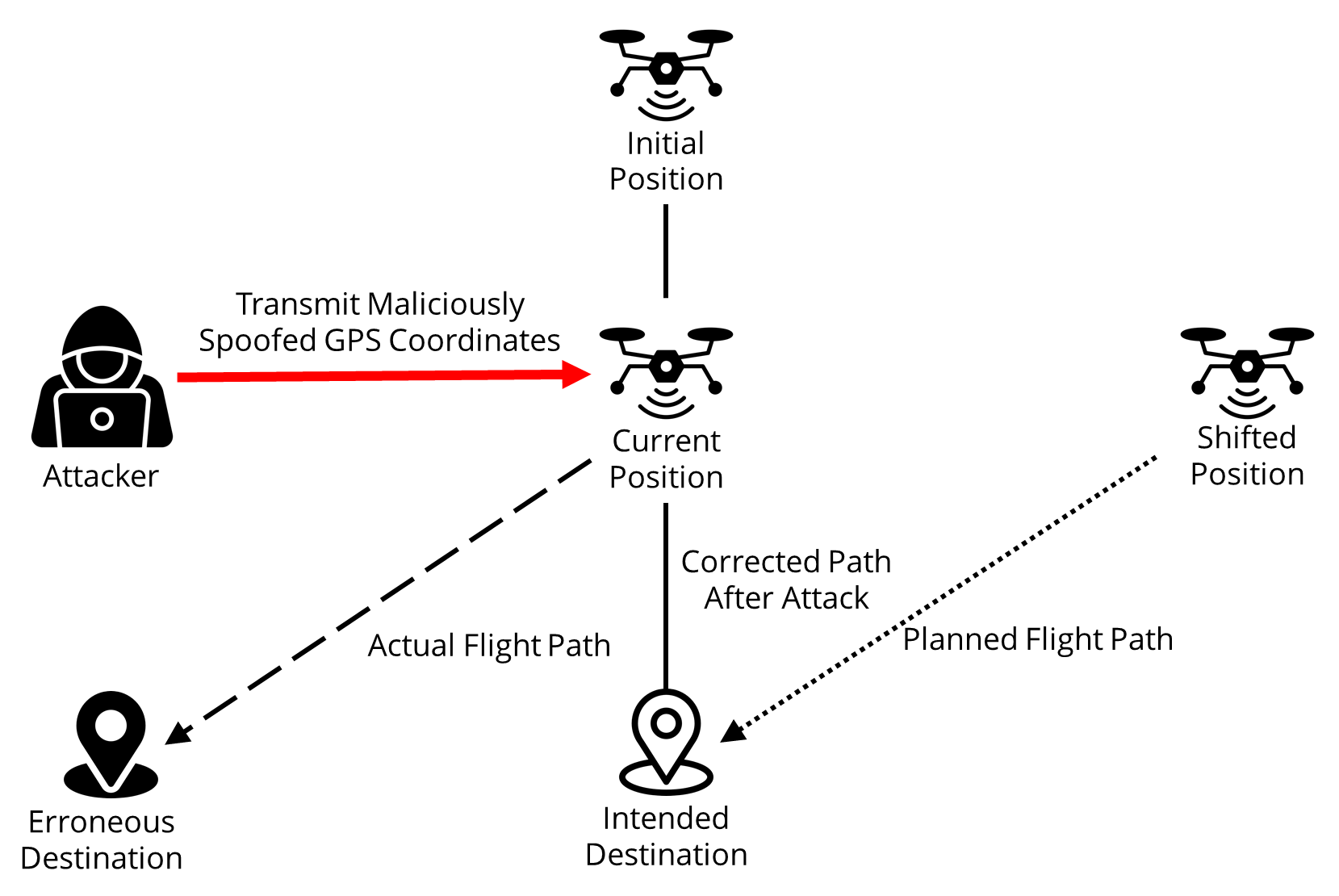
TY - JOUR AU - Liu, Ying-Chen AU - Lee, Lin-Fa AU - Yeh, Kuo-Hui PY - 2025 DA - 2025/12/28 TI - Enhancing UAV Security with GPS Spoofing and Jamming Anomaly Detection JO - Journal of Reliable and Secure Computing T2 - Journal of Reliable and Secure Computing JF - Journal of Reliable and Secure Computing VL - 1 IS - 1 SP - 54 EP - 67 DO - 10.62762/JRSC.2025.368867 UR - https://www.icck.org/article/abs/JRSC.2025.368867 KW - anomaly detection KW - extreme gradient boosting (XGBoost) KW - network security KW - unmanned aerial vehicle (UAV) AB - Unmanned aerial vehicles face GPS spoofing and jamming that can compromise navigation and safety. We present an anomaly detection method that achieves both high accuracy and interpretability, enabling UAV operators to understand why an alert is triggered, which enables timely responses and builds trust in autonomous detection systems operating in safety-critical environments. We use five classifiers, including XGBoost, Support Vector Machine, K-Nearest Neighbor, Random Forest, and Naive Bayes, trained on a UAV dataset containing 3622 samples for spoofing detection and 6445 for jamming detection made in PX4 and Gazebo with benign flight and attack cases. After feature scaling and reduction, XGBoost reaches F1 near 0.998 for both attacks and runs fast enough for small onboard computers. Our main goal is to explain what the models learn. We study feature importance in four ways using gain in XGBoost, impurity decrease in Random Forest, permutation tests for Support Vector Machine and K-Nearest Neighbor, and a closed form score for Naive Bayes. The results point to the same key signals across models. Spoofing shows up as position drift and a mismatch between speed and course. Jamming shows up as sharp growth in position and velocity errors and poor satellite geometry. These insights help operators watch the right signals and trust the alerts. SN - 3070-6424 PB - Institute of Central Computation and Knowledge LA - English ER -
@article{Liu2025Enhancing,
author = {Ying-Chen Liu and Lin-Fa Lee and Kuo-Hui Yeh},
title = {Enhancing UAV Security with GPS Spoofing and Jamming Anomaly Detection},
journal = {Journal of Reliable and Secure Computing},
year = {2025},
volume = {1},
number = {1},
pages = {54-67},
doi = {10.62762/JRSC.2025.368867},
url = {https://www.icck.org/article/abs/JRSC.2025.368867},
abstract = {Unmanned aerial vehicles face GPS spoofing and jamming that can compromise navigation and safety. We present an anomaly detection method that achieves both high accuracy and interpretability, enabling UAV operators to understand why an alert is triggered, which enables timely responses and builds trust in autonomous detection systems operating in safety-critical environments. We use five classifiers, including XGBoost, Support Vector Machine, K-Nearest Neighbor, Random Forest, and Naive Bayes, trained on a UAV dataset containing 3622 samples for spoofing detection and 6445 for jamming detection made in PX4 and Gazebo with benign flight and attack cases. After feature scaling and reduction, XGBoost reaches F1 near 0.998 for both attacks and runs fast enough for small onboard computers. Our main goal is to explain what the models learn. We study feature importance in four ways using gain in XGBoost, impurity decrease in Random Forest, permutation tests for Support Vector Machine and K-Nearest Neighbor, and a closed form score for Naive Bayes. The results point to the same key signals across models. Spoofing shows up as position drift and a mismatch between speed and course. Jamming shows up as sharp growth in position and velocity errors and poor satellite geometry. These insights help operators watch the right signals and trust the alerts.},
keywords = {anomaly detection, extreme gradient boosting (XGBoost), network security, unmanned aerial vehicle (UAV)},
issn = {3070-6424},
publisher = {Institute of Central Computation and Knowledge}
}
 Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.
Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. 
Portico
All published articles are preserved here permanently:
https://www.portico.org/publishers/icck/