ICCK Transactions on Emerging Topics in Artificial Intelligence
ISSN: 3068-6652 (Online)
Email: [email protected]


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
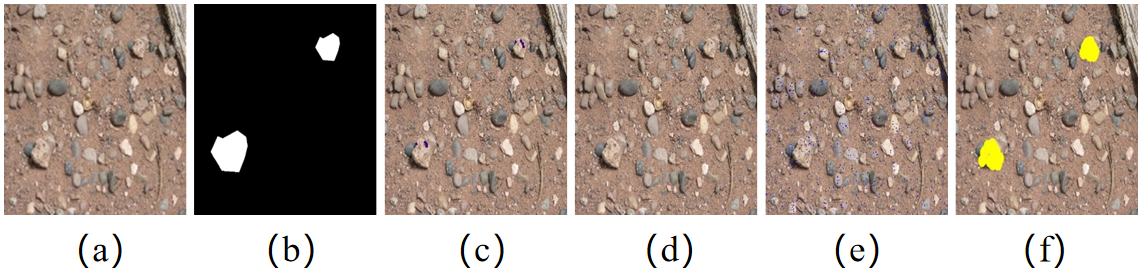
TY - JOUR AU - Abbass, Muhammad Jamshed AU - Waqar, Ali AU - Seemab, Natasha AU - Khan, Abdul Saboor AU - Riaz, Muhammad Bilal AU - Abbas, Sharjeel AU - Mushtaq, Bilal PY - 2025 DA - 2025/11/25 TI - Fast and Robust Copy-Move Forgery Detection Using BRIEF, FAST, and SIFT Feature Matching JO - ICCK Transactions on Emerging Topics in Artificial Intelligence T2 - ICCK Transactions on Emerging Topics in Artificial Intelligence JF - ICCK Transactions on Emerging Topics in Artificial Intelligence VL - 3 IS - 1 SP - 9 EP - 19 DO - 10.62762/TETAI.2025.152706 UR - https://www.icck.org/article/abs/TETAI.2025.152706 KW - hybrid FAST-BRIEF-SIFT KW - g2NN matching KW - LSC-SSIM segmentation KW - copy-move forgery detection KW - deepfake localization KW - satellite image authentication KW - real-time forensics KW - f-measure optimization AB - This paper presents a novel hybrid copy–move forgery detection method that combines the efficiency of FAST-BRIEF (for rapid keypoint detection and binary descriptors) with the robustness of SIFT (for scale- and rotation-invariant feature matching). The proposed framework employs g2NN matching for accurate feature correspondence, followed by morphological processing and LSC-SSIM superpixel segmentation for precise localization of tampered regions. The method is evaluated on 30 diverse test images from benchmark datasets comprising over 700 images, achieving a 95% F-measure with an average CPU time of 6.02 seconds. It demonstrates strong resilience to geometric transformations (rotation, scaling), photometric adjustments (contrast, brightness), additive noise, and multiple forgeries. The proposed methodology offers a 5–30% improvement in accuracy and computational speed. This approach addresses emerging challenges in deepfake detection and satellite imagery authentication, where localized manipulations threaten media integrity. SN - 3068-6652 PB - Institute of Central Computation and Knowledge LA - English ER -
@article{Abbass2025Fast,
author = {Muhammad Jamshed Abbass and Ali Waqar and Natasha Seemab and Abdul Saboor Khan and Muhammad Bilal Riaz and Sharjeel Abbas and Bilal Mushtaq},
title = {Fast and Robust Copy-Move Forgery Detection Using BRIEF, FAST, and SIFT Feature Matching},
journal = {ICCK Transactions on Emerging Topics in Artificial Intelligence},
year = {2025},
volume = {3},
number = {1},
pages = {9-19},
doi = {10.62762/TETAI.2025.152706},
url = {https://www.icck.org/article/abs/TETAI.2025.152706},
abstract = {This paper presents a novel hybrid copy–move forgery detection method that combines the efficiency of FAST-BRIEF (for rapid keypoint detection and binary descriptors) with the robustness of SIFT (for scale- and rotation-invariant feature matching). The proposed framework employs g2NN matching for accurate feature correspondence, followed by morphological processing and LSC-SSIM superpixel segmentation for precise localization of tampered regions. The method is evaluated on 30 diverse test images from benchmark datasets comprising over 700 images, achieving a 95\% F-measure with an average CPU time of 6.02 seconds. It demonstrates strong resilience to geometric transformations (rotation, scaling), photometric adjustments (contrast, brightness), additive noise, and multiple forgeries. The proposed methodology offers a 5–30\% improvement in accuracy and computational speed. This approach addresses emerging challenges in deepfake detection and satellite imagery authentication, where localized manipulations threaten media integrity.},
keywords = {hybrid FAST-BRIEF-SIFT, g2NN matching, LSC-SSIM segmentation, copy-move forgery detection, deepfake localization, satellite image authentication, real-time forensics, f-measure optimization},
issn = {3068-6652},
publisher = {Institute of Central Computation and Knowledge}
}
 Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made.
Copyright © 2025 by the Author(s). Published by Institute of Central Computation and Knowledge. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. ICCK Transactions on Emerging Topics in Artificial Intelligence
ISSN: 3068-6652 (Online)
Email: [email protected]

Portico
All published articles are preserved here permanently:
https://www.portico.org/publishers/icck/